If you are living in a country where some sites are blocked by the server or your office or school colleges have a restricted access to the Internet then this trick may help you in many ways. Most of the colleges and school applied some security firewalls that doesn't allow you to access certain sites. There are lots of options available to access blocked sites such as using proxy sites, VPN servers etc. But local administrator can also block these services also so it is very important for you to know about different tricks to bypass the restrictions. So we are here to help you.
Today we will see another excellent service Hola which can be used to access sites that are blocked by a local administrator. If you want to check the previous post check it here How to access blocked sites using Cocoon.
Today we will see another excellent service Hola which can be used to access sites that are blocked by a local administrator. If you want to check the previous post check it here How to access blocked sites using Cocoon.
What is Hola?
To access blocked sites here is an excellent service named Hola which provides wide variety of services on different platforms. It is free to use VPN service. You can use Hola on your computer as well as on your mobile phones. Hola is a browser extension for Mozilla Firefox, Google Chrome and Internet Explorer. It is also available as an application software for Windows and Mac. Also Android and iOS devices can use Hola to access blocked sites in any public or private network.
How to access blocked sites?
Using Hola to access sites is very simple check out their official website http://hola.org
*. Download Hola as a browser add-on on any browser.
*. After successful installation you will see an icon on top right corner.
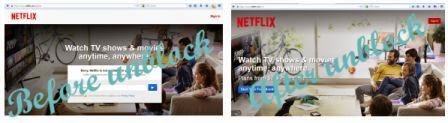
*. Open any blocked site. If you unable to open that site then click on Hola's icon and select the country like US and in a few seconds you may able to access blocked site easily. See the example screenshot below for netflix.com
After unblocking site you will see any country's flag like US from where you are accessing that site and you won't be trapped by anyone. Stay and surf anonymously anywhere.